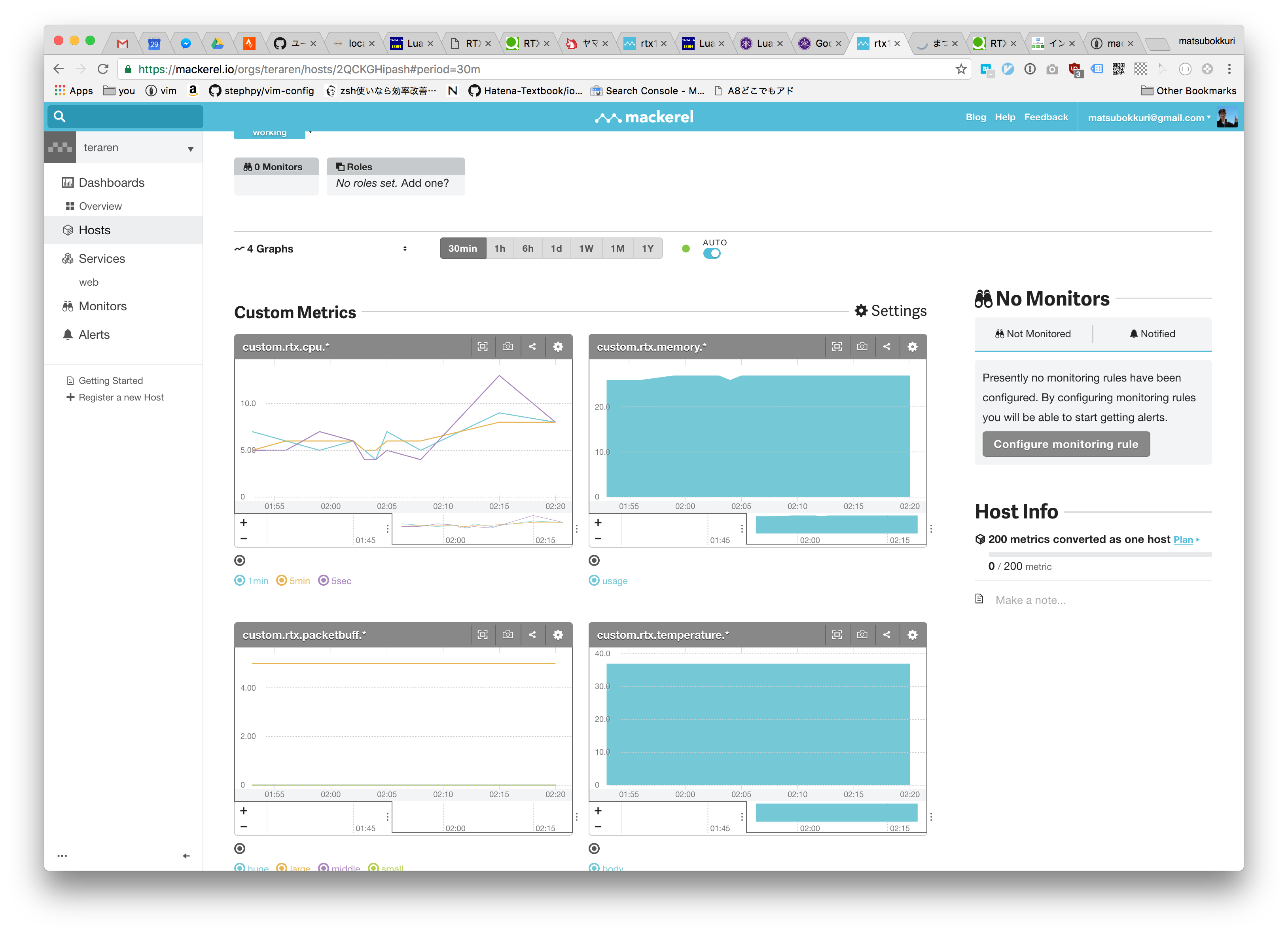
MackerelでRTX1200を監視設定
- 家のRTX1200のリソースを監視します。
https://amzn.to/3BzewF8
- こちらを参考にセットアップしてみました
現在のRTX1200の設定
# RTX1200 Rev.10.01.71 (Thu Sep 29 15:08:40 2016) # MAC Address : 00:a0:de:68:90:0c, 00:a0:de:68:90:0d, 00:a0:de:68:90:0e # Memory 128Mbytes, 3LAN, 1BRI # main: RTX1200 ver=c0 serial=D2F004125 MAC-Address=00:a0:de:68:90:0c MAC-Addr ess=00:a0:de:68:90:0d MAC-Address=00:a0:de:68:90:0e # Reporting Date: Oct 29 02:12:00 2016 ip route default gateway pp 3 ip keepalive 1 icmp-echo 10 5 dhcp lan3 ip lan1 address 192.168.1.1/24 ip lan1 proxyarp on ip lan1 secure filter in 100000 100001 100002 100003 100004 100005 100006 10000 7 100099 ip lan2 secure filter in 102003 102020 102021 102022 102023 102024 102025 10203 0 102032 ip lan2 secure filter out 102013 102020 102021 102022 102023 102024 102025 1020 26 102027 102099 dynamic 102080 102081 102082 102083 102084 102085 102098 10209 9 ip lan2 nat descriptor 299 description lan3 PRV/DHCP/226: lan shutdown lan3 ip lan3 address dhcp ip lan3 secure filter in 102003 102020 102021 102022 102023 102024 102025 10203 0 102032 ip lan3 secure filter out 102013 102020 102021 102022 102023 102024 102025 1020 26 102027 102099 dynamic 102080 102081 102082 102083 102084 102085 102098 10209 9 pp select 3 description pp PRV/PPPoE/2:gmo pp keepalive interval 30 retry-interval=30 count=12 pp always-on on pppoe use lan2 pppoe auto connect on pppoe auto disconnect off pp auth accept pap chap pp auth myname xxxxxxxxxxxxxxxxxx xxxxxxxxxxxxxxxxxxx ppp lcp mru on 1454 ppp ipcp ipaddress on ppp ipcp msext on ppp ccp type none ip pp mtu 1500 ip pp secure filter in 202003 202020 202021 202022 202023 202024 202025 202030 202032 202080 202081 202082 13 14 ip pp secure filter out 202013 202020 202021 202022 202023 202024 202025 20202 6 202027 202099 dynamic 202080 202081 202082 202083 202084 202085 202098 202099 ip pp nat descriptor 1200 pp enable 3 pp select anonymous pp name "pptp server" pp bind tunnel1 pp auth request mschap-v2 pp auth username xxxxxxxxxxxx xxxxxxxxxxxxxxxx ppp ipcp ipaddress on ppp ipcp msext on ip pp remote address pool dhcp ip pp mtu 1258 pp enable anonymous tunnel select 1 tunnel encapsulation l2tp ipsec tunnel 1 ipsec sa policy 1 1 esp aes-cbc sha-hmac ipsec ike keepalive log 1 off ipsec ike keepalive use 1 off ipsec ike nat-traversal 1 on ipsec ike pre-shared-key 1 text xxxxxxxxxxxxxxxxxxxxxxx ipsec ike remote address 1 any l2tp tunnel auth off l2tp tunnel disconnect time off l2tp keepalive use on ip tunnel tcp mss limit auto tunnel enable 1 ip filter 1 pass * 192.168.1.7 tcp * 22,www,https,domain ip filter 2 pass * 192.168.1.7 udp * domain ip filter 3 pass * 192.168.1.1 esp * * ip filter 4 pass * 192.168.1.1 udp * 500 ip filter 5 pass * 192.168.1.1 udp * 4500 ip filter 6 pass * 192.168.1.1 udp * 1701 ip filter 7 pass * 192.168.1.7 tcp * 22,www,https,domain ip filter 8 pass * 192.168.1.7 udp * domain ip filter 9 pass * * esp * * ip filter 10 pass * 192.168.1.7 udp * 500 ip filter 11 pass * 192.168.1.7 udp * 4500 ip filter 12 pass * 192.168.1.7 udp * 1701 ip filter 13 pass * * tcp * 22,www,https,domain ip filter 14 pass * * udp * domain ip filter 100000 reject * * udp,tcp 135 * ip filter 100001 reject * * udp,tcp * 135 ip filter 100002 reject * * udp,tcp netbios_ns-netbios_dgm * ip filter 100003 reject * * udp,tcp * netbios_ns-netbios_dgm ip filter 100004 reject * * udp,tcp netbios_ssn * ip filter 100005 reject * * udp,tcp * netbios_ssn ip filter 100006 reject * * udp,tcp 445 * ip filter 100007 reject * * udp,tcp * 445 ip filter 100099 pass * * * * * ip filter 102000 reject 10.0.0.0/8 * * * * ip filter 102001 reject 172.16.0.0/12 * * * * ip filter 102002 reject 192.168.0.0/16 * * * * ip filter 102003 reject 192.168.1.0/24 * * * * ip filter 102010 reject * 10.0.0.0/8 * * * ip filter 102011 reject * 172.16.0.0/12 * * * ip filter 102012 reject * 192.168.0.0/16 * * * ip filter 102013 reject * 192.168.1.0/24 * * * ip filter 102020 reject * * udp,tcp 135 * ip filter 102021 reject * * udp,tcp * 135 ip filter 102022 reject * * udp,tcp netbios_ns-netbios_ssn * ip filter 102023 reject * * udp,tcp * netbios_ns-netbios_ssn ip filter 102024 reject * * udp,tcp 445 * ip filter 102025 reject * * udp,tcp * 445 ip filter 102026 restrict * * tcpfin * www,21,nntp ip filter 102027 restrict * * tcprst * www,21,nntp ip filter 102030 pass * 192.168.1.0/24 icmp * * ip filter 102031 pass * 192.168.1.0/24 established * * ip filter 102032 pass * 192.168.1.0/24 tcp * ident ip filter 102033 pass * 192.168.1.0/24 tcp ftpdata * ip filter 102034 pass * 192.168.1.0/24 tcp,udp * domain ip filter 102035 pass * 192.168.1.0/24 udp domain * ip filter 102036 pass * 192.168.1.0/24 udp * ntp ip filter 102037 pass * 192.168.1.0/24 udp ntp * ip filter 102099 pass * * * * * ip filter 103000 pass * * tcp * 8000 ip filter 202000 reject 10.0.0.0/8 * * * * ip filter 202001 reject 172.16.0.0/12 * * * * ip filter 202002 reject 192.168.0.0/16 * * * * ip filter 202003 reject 192.168.1.0/24 * * * * ip filter 202010 reject * 10.0.0.0/8 * * * ip filter 202011 reject * 172.16.0.0/12 * * * ip filter 202012 reject * 192.168.0.0/16 * * * ip filter 202013 reject * 192.168.1.0/24 * * * ip filter 202020 reject * * udp,tcp 135 * ip filter 202021 reject * * udp,tcp * 135 ip filter 202022 reject * * udp,tcp netbios_ns-netbios_ssn * ip filter 202023 reject * * udp,tcp * netbios_ns-netbios_ssn ip filter 202024 reject * * udp,tcp 445 * ip filter 202025 reject * * udp,tcp * 445 ip filter 202026 restrict * * tcpfin * www,21,nntp ip filter 202027 restrict * * tcprst * www,21,nntp ip filter 202030 pass * 192.168.1.0/24 icmp * * ip filter 202031 pass * 192.168.1.0/24 established * * ip filter 202032 pass * 192.168.1.0/24 tcp * ident ip filter 202033 pass * 192.168.1.0/24 tcp ftpdata * ip filter 202034 pass * 192.168.1.0/24 tcp,udp * domain ip filter 202035 pass * 192.168.1.0/24 udp domain * ip filter 202036 pass * 192.168.1.0/24 udp * ntp ip filter 202037 pass * 192.168.1.0/24 udp ntp * ip filter 202080 pass * 192.168.1.1 esp * * ip filter 202081 pass * 192.168.1.1 udp * 500 ip filter 202082 pass * 192.168.1.1 udp * 4500 ip filter 202099 pass * * * * * ip filter 500000 restrict * * * * * ip filter dynamic 102080 * * ftp ip filter dynamic 102081 * * domain ip filter dynamic 102082 * * www ip filter dynamic 102083 * * smtp ip filter dynamic 102084 * * pop3 ip filter dynamic 102085 * * submission ip filter dynamic 102098 * * tcp ip filter dynamic 102099 * * udp ip filter dynamic 202080 * * ftp ip filter dynamic 202081 * * domain ip filter dynamic 202082 * * www ip filter dynamic 202083 * * smtp ip filter dynamic 202084 * * pop3 ip filter dynamic 202085 * * submission ip filter dynamic 202098 * * tcp ip filter dynamic 202099 * * udp nat descriptor type 1 masquerade nat descriptor address outer 1 ipcp nat descriptor address inner 1 auto nat descriptor masquerade static 1 1 192.168.1.1 esp nat descriptor masquerade static 1 2 192.168.1.1 udp 500 nat descriptor masquerade static 1 3 192.168.1.1 udp 4500 nat descriptor type 299 masquerade nat descriptor address outer 299 primary nat descriptor type 1000 nat-masquerade nat descriptor type 1200 masquerade nat descriptor masquerade static 1200 1 192.168.1.7 tcp www nat descriptor masquerade static 1200 2 192.168.1.7 udp domain nat descriptor masquerade static 1200 3 192.168.1.7 tcp domain nat descriptor masquerade static 1200 4 192.168.1.7 tcp 22 nat descriptor masquerade static 1200 5 192.168.1.7 tcp https nat descriptor masquerade static 1200 6 192.168.1.7 esp nat descriptor masquerade static 1200 7 192.168.1.7 udp 4500 nat descriptor masquerade static 1200 8 192.168.1.7 udp 500 nat descriptor masquerade static 1200 9 192.168.1.7 tcp 9001 ipsec auto refresh on ipsec transport 1 1 udp 1701 syslog notice on syslog info off tftp host 192.168.1.101 dhcp service server dhcp server rfc2131 compliant except remain-silent dhcp scope 1 192.168.1.100-192.168.1.254/24 dns server pp 3 dns server select 500003 pp 3 any . restrict pp 3 dns server select 500227 dhcp lan3 any . dns private address spoof on snmp sysname yamaha-rtx1200-00a0de68900c schedule at 1 startup * lua mackerel.lua l2tp service on httpd host lan1 upnp use on statistics cpu on statistics memory on statistics traffic on statistics flow on statistics route on statistics nat on statistics filter on lua use on
luaファイル。RTX1200へtftpで転送して、実行する。
sjisで保存する必要があります。
-------------------------- ## 設定値 ##--------------------------------
-- 監視間隔(1 - 864000 秒)
-- 5分以上の間隔にすると Mackerel の Connectivity アラートが上がるので監視から外すか5分未満にする
idle_time = 60
-- os.time と unix time のオフセット(秒)
os_time_offset = 315532800;
-- Mackerel API に向けた http プロキシのエンドポイントURL
proxy_tsdb = "http://rtx1200.teraren.com/api/v0/tsdb"
-- Mackerel で実行端末用に作成した hostId
-- @see http://help-ja.mackerel.io/entry/spec/api/v0#host-create
host = "2QCKGHipash"
---------------------- ## 設定値ここまで ##----------------------------
------------------------------------------------------------
-- ルーターのハードウェアリソースの使用状況を取得する関数 --
-- サンプルからありがたく拝借
------------------------------------------------------------
function rt_res_status(table)
local rtn, str
local cmd = "show environment"
rtn, str = rt.command(cmd)
if (rtn) and (str) then
for k, v in pairs(table) do
v.val = str:match(v.ptn)
if (v.val) then
v.val = tostring(v.val)
end
end
else
str = cmd .. "コマンド実行失敗\r\n\r\n"
end
return rtn, str
end
------------------------------------------------------------
-- Mackerel 向けの MetricValue API Post 文字列生成 --
-- @see http://help-ja.mackerel.io/entry/spec/api/v0#metric-value-post
------------------------------------------------------------
function make_post_text(host, time, table)
local a = "";
for k, v in pairs(table) do
a = a .. string.format("{\"hostId\":\"%s\",\"name\":\"%s\",\"value\":%s,\"time\":%d}", host, v.name, v.val, time) .. ","
end
return "[" .. string.sub(a,1,-2) .. "]"
end
------------------------------------------------------------
-- メインルーチン --
------------------------------------------------------------
-- ハードウェアリソース情報テーブル
local rt_res_tbl = {
cpu_5sec = { ptn = "(%d+)%%%(5sec%)", val = 0 , name = "custom.rtx.cpu.5sec"},
cpu_1min = { ptn = "(%d+)%%%(1min%)", val = 0 , name = "custom.rtx.cpu.1min"},
cpu_5min = { ptn = "(%d+)%%%(5min%)", val = 0 , name = "custom.rtx.cpu.5min"},
memory = { ptn = "(%d+)%% used", val = 0 , name = "custom.rtx.memory.usage"},
packet_small = { ptn = "(%d+)%%%(small%)", val = 0 , name = "custom.rtx.packetbuff.small"},
packet_middle = { ptn = "(%d+)%%%(middle%)", val = 0 , name = "custom.rtx.packetbuff.middle"},
packet_large = { ptn = "(%d+)%%%(large%)", val = 0 , name = "custom.rtx.packetbuff.large"},
packet_huge = { ptn = "(%d+)%%%(huge%)", val = 0 , name = "custom.rtx.packetbuff.huge"},
temp = { ptn = "筐体内温度%(℃%): (%d+)", val = 0 , name = "custom.rtx.temperature.body"}
}
-- HTTPリクエスト用テーブル
local http_req_tbl = {
url = proxy_tsdb,
method = "POST",
content_type = "application/json"
}
local rtn, str, num, now
while (true) do
-- リソースの取得
rtn, str = rt_res_status(rt_res_tbl)
-- 現在時刻をエポック秒にする
now = os.time() + os_time_offset
-- コマンド失敗時は処理しない(Mackerel の Connectivity アラートを上げさせる)
if (rtn) then
-- リクエストを発行
http_req_tbl.post_text = make_post_text(
host,
now,
rt_res_tbl
)
rt.httprequest(http_req_tbl)
-- http_res_tbl = rt.httprequest(http_req_tbl)
-- print(http_req_tbl.post_text)
-- print(http_res_tbl.body)
end
rt.sleep(idle_time)
end
LANにあるnginxの設定
server{
listen 80;
server_name rtx1200.teraren.com;
access_log /var/log/nginx/rtx1200.teraren.com main;
location / {
proxy_pass https://mackerel.io;
proxy_set_header X-Api-key xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx;
proxy_ssl_session_reuse off;
allow 192.168.1.0/24;
allow 222.230.108.57;
deny all;
}
}
追記
夏は熱くなるなぁ。。。
密閉されているところにおいてあるから厳しそう。




Comments